Six tips for remote HMI/SCADA users to protect plant operations, drive cost savings
When you wake up in the morning, you can program your coffee maker upstairs with your smartphone and get a notification when your cup of coffee is done brewing downstairs. You can also turn up the thermostat with the touch of your phone to increase the temperature before you even get out of bed. This technology is part of the Internet of Things and it is helping to make people’s everyday lives more convenient and efficient.
The Internet of Things revolves around increased machine-to-machine (M2M) communication, and is built on cloud computing and networks of data-gathering sensors. Beyond our daily lives at home, this concept is also becoming widely used in the industrial sector and has been dubbed the Industrial Internet of Things (IIoT). Now M2M technology allows us to manage and monitor equipment remotely and address problems in a timely manner, which also translates to cost savings. In fact, the average field service visit costs more than $1,000 according to data from the Technology Services Industry Association, and every eliminated field visit adds to an organization's bottom line.
A variety of M2M solutions are available that can help diagnose and fix equipment issues, including remote desktop that allows users to manage the machine/process remotely as if they were standing in front of a human-machine interface (HMI) connected to a supervisory control and data acquisition (SCADA) system. (HMI/SCADA solutions have become a widely used tool in a variety of industries, and are often at the heart of an operation’s data visualization, control, and reporting process to drive operational improvements.) A development software interface enables users to connect remotely to HMI/SCADA systems in order to make machine/process changes over the Internet without forcing unnecessary shutdowns.
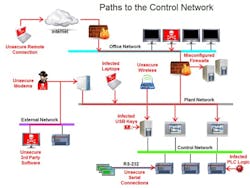
While remote monitoring solutions like HMI can provide cost-savings and increased efficiency, it’s important to understand the security risks associated with this technology and how to protect against them. Past cybersecurity breaches have shown how harmful cyberattacks can be for remote activity operations in the industrial sector. For example, the Stuxnet virus is a computer worm that targeted industrial control systems that are used to monitor and control large-scale industrial facilities like power plants, dams, waste processing systems, and similar operations. The virus allows the attackers to take control of these systems without the operators knowing, and the hackers can manipulate real-world equipment. Due to Stuxnet-type viruses and other various cyber threats, there’s been an increased emphasis on HMI/SCADA security and users of HMI/SCADA systems are focusing on how to protect this key element of their operations.
[sidebar id="1"]
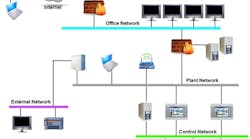
Figure 1. Paths to the Control Network from an Engineer’s Perspective
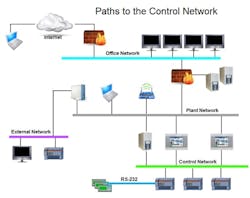
Figure 2. Paths to the Control Network from a Corporate IT Manager’s Perspective
The good news is that there are a variety of ways to secure remote access and reduce cybersecurity risks while enabling the connectivity required to support and service equipment. Users of HMI/SCADA systems can employ the following methods to help protect their systems:
- Look for a system with robust built-in security, which is the last line of defense against unwanted access. Some of the systems allow you to tie the SCADA security into the plant security system through a Lightweight Directory Access Protocol (LDAP) interface to Microsoft’s Active Directory server.
- Firewalls are key to keeping a network secure. They can either be software-based or hardware-based, and their primary objective is to control the incoming and outgoing network traffic. Firewalls are designed to analyze the data packets and determine whether they should be allowed to pass or not, based on a predetermined rule set. Most routers that pass data between networks contain firewalls and/or firewall components. Secure socket layer (SSL) encryption is important to help prevent unwanted access to information about the machine. This addresses security between outgoing email and incoming (i.e., HTTPS) network access.
- Virtual private networks (VPN) use the Internet to connect computers to isolated remote computer networks that would otherwise be inaccessible. A VPN provides security so that traffic sent through the VPN connection stays isolated from other computers on the network. Some routers can create one or more VPNs that allow secure connections from the Internet to computers within a plant network.
- Deep Packet Inspection (DPI) is a form of network packet filtering that examines the data portion of a packet as it passes an inspection point, searching for protocol non-compliance, viruses, spam, intrusions, or other defined criteria. It can then decide whether the packet may pass, be blocked, or be routed to a different destination. Certain routers and passive network devices that are commercially available incorporate this technology to filter messages at the application protocol layer (e.g., Modbus TCP or EtherNet/IP).
- Segmenting the network into functional areas using intelligent routers provides additional layers of security. The more layers of security, the more difficult it is for cyber-criminals to compromise the security of the manufacturing line and its control system. In addition, network segmentation provides a mechanism to isolate the control system from a plant or office network by providing an “air gap” in the event that other segments of the network are under attack. Unplugging the router’s uplink to the rest of the network kills remote connectivity, but it allows the manufacturing line to continue to run in this worst-case scenario.
- Some Windows-based HMI/SCADA systems offer a protected, non-corruptible operating system. In the event that the machines do contract a virus or other malware, the problem can be cleared with a simple reboot. Despite all of the network security measures, an engineer or operator can still introduce a virus into the network by simply plugging an infected USB memory stick into a PC behind the firewall. A reboot will get the machine running much more quickly than a backup to a restore point, assuming a good restore point is even available.
HMI/SCADA systems provide remarkable efficiently and cost-savings for users and OEMs, but ensuring the security of the systems while protecting against cyber threats is crucial. Companies can first start by selecting systems with inherent security designs that can protect against a malware attack. Additionally, taking proactive steps such as working with IT to design the network interfaces and firewalls can help to minimize internal and external risks. Ultimately, these safeguards can help companies enhance the protection of their critical infrastructure assets and reduce costs.
[sidebar id="2"]